By: Jason Haddix, CISO
For our first technical blog, we wanted to share something that our peers in the Red Team and Adversarial Emulation/Simulation industry could utilize and implement within their teams.
When you’re attempting to emulate the adversary, you have to keep up with external tactics where you try to gain access from the external Internet, and internal tactics for when access is successful. We’ve found the evolution of red teaming has grown to count on phishing as the prime method of initial access. While we love a good phish, we also enjoy the challenge of breaking in from the external portion of a campaign. This involves an external vulnerability analysis of our client’s attack surface and this approach mirrors what we see with highly-skilled modern adversaries in the real world.
Logistically, when you’re on the external portions of a red team campaign, you may struggle with different layers of security protections hindering your tactics. This could be:
- A modern client using a CDN with security features that blocks or blacklists your testing infrastructure
- A solid WAF at the web application or web framework level
- An external network monitored by the client SOC noticing you probing them in various ways
So, if we want to do things in our campaigns like probe external infrastructure, fuzz web applications, or brute force services, what can we do to keep our team efficient and stealthy?
We evaluated numerous tools for our methodology and put together the following resources. Red teams should evaluate the different tool options so they can choose what works best for their testing infrastructure.
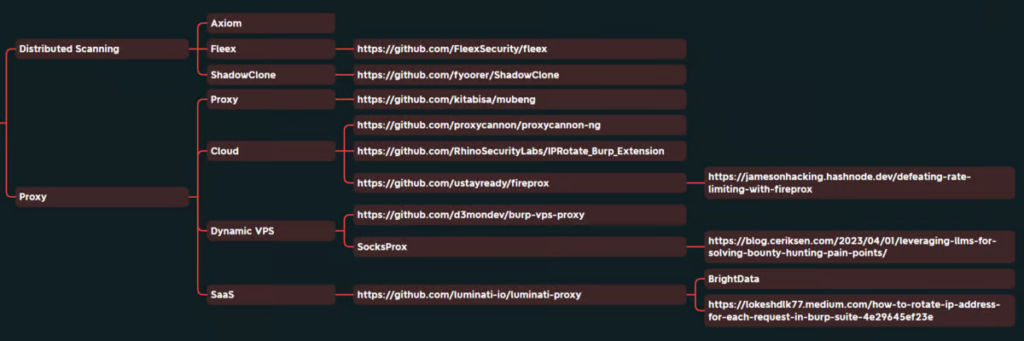
In general, there are two categories of TTPs we can use to help our efficiency and stealth when external testing:
Distributed Scanning
One set of techniques that teams need to be incorporating is new-school distributed scanning. Distributed scanning allows you to divide large brute-forcing tasks, content discovery, and scan tasks across multiple hosts. This can reduce what would take hours of scanning down to minutes. These tools will take a large fuzzing file, break it up into smaller chunks and run it from different machines. While an auxiliary benefit of these tools is that they allow you to remain somewhat stealthy, that is not their primary purpose.
One of the clear frontrunners in distributed scanning is Shadow Clone due to its ease of use and ability to utilize cost-effective cloud technologies.
From the Repo:
ShadowClone allows you to distribute your long-running tasks dynamically across thousands of serverless functions and gives you the results within seconds where it would have taken hours to complete.
Other distribution frameworks we have worked with are:
- Axiom – https://twitter.com/Jhaddix/status/1633936278222962688
- Fleex – https://github.com/FleexSecurity/fleex
Proxying Requests for Web or Credentialed Attacks
The other set of tools is for proxying individual requests, typically during a credential spray, web fuzzing, etc. This allows you to constantly change where you are coming from and stay under the radar.
In this category, you have tools that obscure where you’re coming from via regular proxies, cloud instances, dynamic VPS setups, and some even proxy through SaaS platforms.
In this area, Fireprox by Black Hills Information Security and IP Rotate Burp Extension are our standard choices. However, if you are looking for ease of use for web testing and only need to switch to one new IP address, Burp VPS Proxy is quite impressive.
James Gallagher wrote an excellent blog on “Defeating Rate Limiting with Fireprox”
IP Rotate Burp Extension in action…
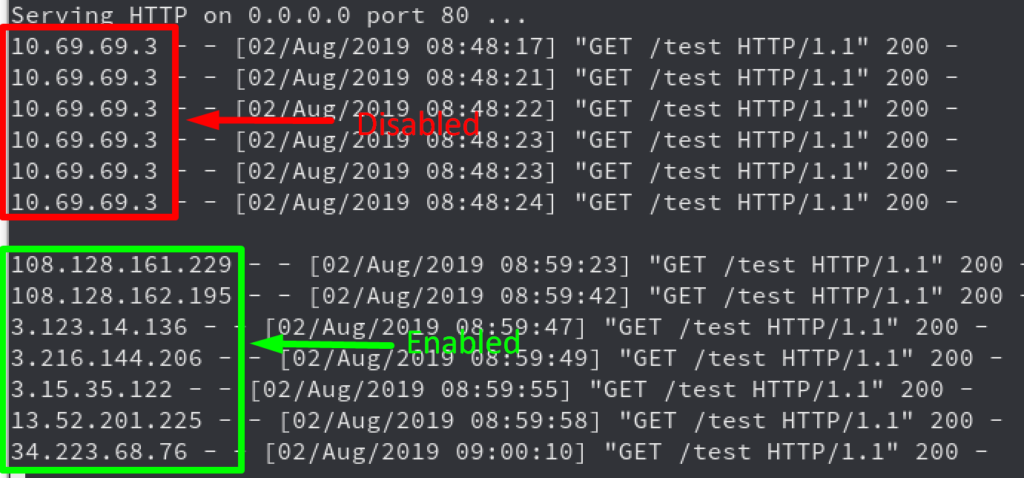
Here’s the list of working tools out of the many we evaluated. While everything on this list works, we chose the ones above as our frontrunners.
Socks Proxying
Cloud
- https://github.com/proxycannon/proxycannon-ng
- https://github.com/RhinoSecurityLabs/IPRotate_Burp_Extension
- https://github.com/ustayready/fireprox
Dynamic VPS
- Web – https://github.com/d3mondev/burp-vps-proxy
- SocksProx – https://blog.ceriksen.com/2023/04/01/leveraging-llms-for-solving-bounty-hunting-pain-points/
Saas
Running through all of these tools and frameworks was a fun exercise when we were first standing up our methodology. We want to thank the tool authors and all of the hard work they put into maintaining these open-source projects for red teamers. We hope the time we took to pare down the large assortment of tools emerging in this area helps your testing team in their daily operations.
Until next time – happy hacking!
About Jason Haddix, CISO

Jason has had a distinguished 15-year career in cybersecurity previously serving as the CISO of Ubisoft, Head of Trust/Security/Operations at Bugcrowd, Director of Penetration Testing at HP, and Lead Penetration Tester at Redspin. He’s a hacker and bug hunter to the core, ranking 51st all-time on Bugcrowd’s leaderboards. Jason has also authored many talks and has spoken at cons such as DEFCON, Black Hat, OWASP, RSA, Nullcon, SANS, and many more.
