By: Jason Haddix, CISO
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is extremely important. One crucial aspect of this is maintaining a strong defense against external attacks. Enter Easy EASM, a tool for organizations to manage their attack surface with minimal effort and zero cost. Developed by the expert trio – Jason Haddix, Gunnar Andrews, and Olivia Gallucci – this tool is made for both security professionals and businesses looking to enhance their cybersecurity posture.
Unveiling Easy ASM: A Brief Overview
The cybersecurity industry is no stranger to External Attack Surface Management (EASM) tools. However, Easy EASM takes a fresh approach. Built on the bedrock of the bug bounty scene and leveraging the expertise of its creators, Easy EASM brings simplicity and efficiency. The tool’s core mission is to provide organizations with visibility into their external-facing assets – a task that’s crucial for proactive threat mitigation.
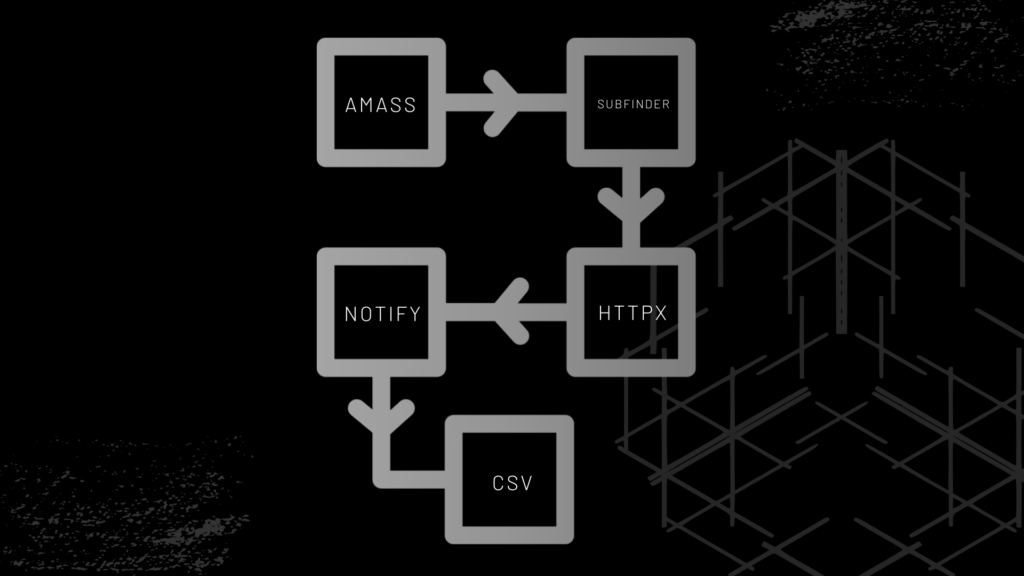
With just a few lines of setup and a simple deployment process, users can gain a comprehensive view of their online assets. The tool utilizes a suite of open-source tools, including Amass, Subfinder, Chaos, Notify, and more, expertly woven together to perform effective reconnaissance on specified targets.
The cherry on top is the daily scanning mechanism coupled with real-time alerts delivered via Slack or Discord for newly discovered assets. Furthermore, Easy EASM goes the extra mile by generating an Excel-based Asset Database skeleton, streamlining the data presentation process for IT.
The Genesis of Easy ASM: Tackling a Common Problem
The idea behind Easy EASM was born from the experiences of seasoned bug bounty hunters and red teamers. They all recognized a glaring issue – the challenge of tracking and managing an organization’s internet-facing assets. The complexities of modern business operations can cause IT and Security groups to lose track of assets (also known as shadow IT). Some examples:
- Acquisitions
- Rogue IT or development initiatives where development teams spin out some Cloud infrastructure.
- Marketing teams buy a license to a SaaS and set up a subdomain.
The Easy ASM tool sets out to address this problem, providing a user-friendly solution to prevent the loss of visibility into an organization’s attack surface.

From Hackers to Enterprises
The innovation behind Easy EASM draws inspiration from the hacker community’s approach to reconnaissance. Before the era of sophisticated ASM tools, hackers relied on brute-force methods and tools like Fierce to discover subdomains and assets. Over time, the landscape evolved, leading to the creation of tools like Sublist3r, Amass, and SubFinder, which scrape information from various internet sources to build a comprehensive picture.
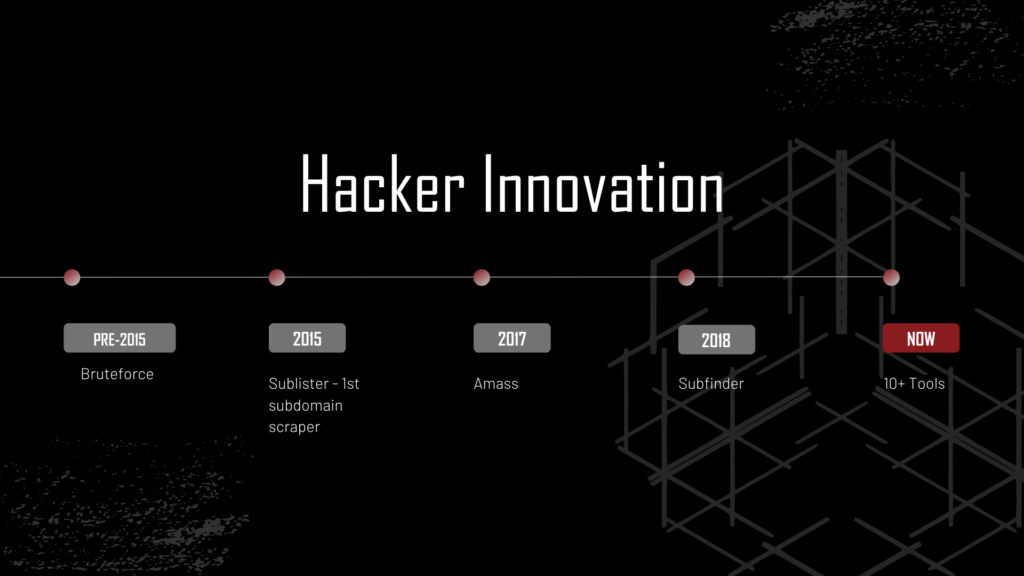
Enterprises started to realize that there was a need for these tools. A lot of companies wanted to track their assets and they wanted to be able to do so easily. This led to numerous for-pay companies taking open-source tools, combining them, and putting them into a proprietary wrapper. Then these EASM companies charged thousands upon thousands of dollars to use them.
Commercial EASM
We researched external attack surface management platforms, and how they break out what they do. What we started to see in the attack surface management industry is that it wasn’t enough anymore just to give you subdomains and assets. These new EASM vendors couldn’t justify the costs of their platforms and had to add vulnerability scanning and esoteric methods of discovering different risks that are not assets. They also started to include threat Intel into their packages.

During our investigations, several commercial attack surface management platforms sold today were being sold for 60-100 dollars a year. Many only gave IP/asset information, hosting data, and cursory vulnerability scanning.
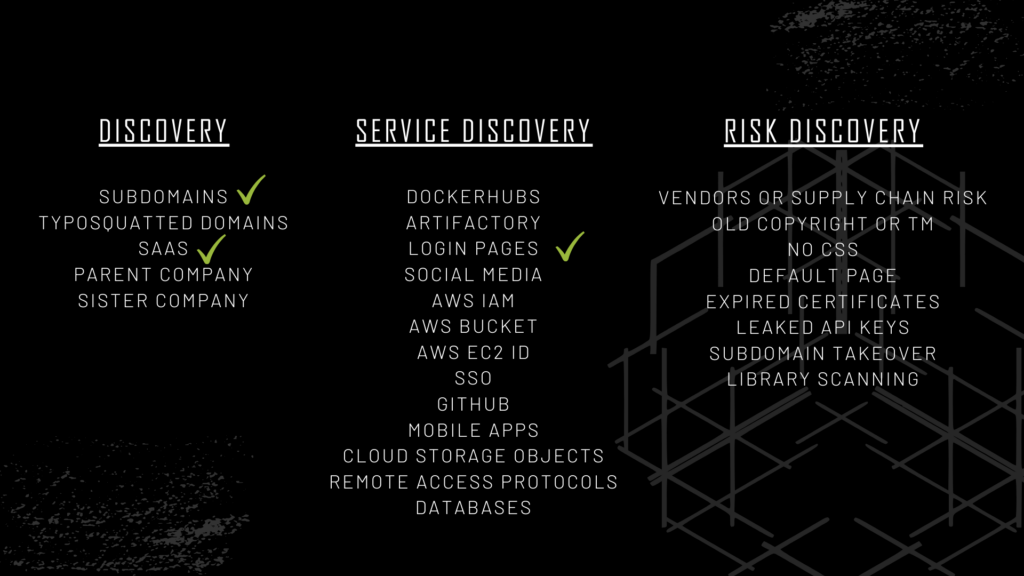
Easy ASM is the solution that bridges the gap for IT. By combining the power of Amass and ProjectDiscovery.io tools, we created a tool that’s not only easy to use but also delivers high-quality results. The tool’s design accommodates two run types: a faster mode for hitting APIs and larger domains, and a more comprehensive active mode where you would give a word list, set up a thread count, deploy the tool, and let it run for a long time. It will add your active enumeration, recursive enumeration, and permutation scanning.
We’ve started with the green checkmarks, but you can do everything with open-source tools. Our plan is to make this tool as easy to run as possible and to give you guys the power to do all these things.
Easy ASM’s Features and Output
Easy ASM’s output is a comprehensive CSV file that includes vital information about the discovered assets. This includes details like runtime, timestamp, ASN data, URL data, titles, HTTP titles, web server information, IP addresses, CNAMEs, technology fingerprints, return status codes, and more. The tool also has the capability to send notifications via Slack or Discord webhooks. These notifications include updates on new domains as well as assets that were previously present but have disappeared from the internet. This is a tool that you can run as many times as you want, and you’ll always have an up-to-date list of assets that you have on the internet.
The Roadmap Ahead
Easy ASM is more than just a tool; it’s a living project with a roadmap that extends into the future. Starting with Version 1, the tool’s creators plan to expand its capabilities to cover not only domains and DNS information but also a wider range of features. This roadmap emphasizes community involvement, inviting contributors to build upon the framework and enhance its capabilities further. Our current main goal is to make sure the tool works with Amass 2.0 and its’ new syntax and structure.
In a world where cybersecurity threats continue to evolve, Easy ASM hopes to empower organizations to regain control over their external attack surface. With its simple setup, real-time alerts, and comprehensive asset discovery, Easy ASM proves that effective cybersecurity doesn’t have to come at a high cost. It’s a tool that levels the playing field, making it easier than ever for organizations to defend against external threats and ensure their online assets remain secure.
Tool: https://github.com/g0ldencybersec/EasyEASM
DEF CON 31 – Recon Village Talk (below)
About Jason Haddix, CISO

Jason has had a distinguished 15-year career in cybersecurity previously serving as the CISO of Ubisoft, Head of Trust/Security/Operations at Bugcrowd, Director of Penetration Testing at HP, and Lead Penetration Tester at Redspin. He’s a hacker and bug hunter to the core, ranking 51st all-time on Bugcrowd’s leaderboards. Jason has also authored many talks and has spoken at cons such as DEFCON, Black Hat, OWASP, RSA, Nullcon, SANS, and many more.
