Gone are the days of one and done...
If you’ve ever been involved in a security breach, you know that even the best defenses can fail. Point-in-time security testing doesn’t cut it when adversaries seek to breach companies 24/7. The last few years have been eye-opening as some of the more widely known household companies have been breached. BuddoBot has been intimately involved in the recovery and remediation of some of these breaches, and we have a deep understanding of what makes companies vulnerable to breaches and the most effective measures to prevent them.
Continuous Adversary Emulation
Continuous Matters
Adversaries never sleep. We provide real-world and customized testing campaigns at the ready. Our Continuous Adversary Emulation (CAE) is an industry-leading, non-automated, annual service designed to bring the best offensive cybersecurity services, expertise, and tools the security space has to offer into one custom-tailored continuous solution. Dive into the importance and overview of each CAE component below.
Attack Surface Management
Threat Intelligence
Advanced Social Engineering
External Threat Campaign
Assumed Breach Campaign
Penetration Testing

What Breaches Have in Common
Many modern breaches don’t follow traditional security testing patterns, enabling them to bypass common best-practice defenses and leave organizations feeling helpless. That’s where we come in. BuddoBot is your red team as a service, helping your security team to understand points of exposure and weakness so you can move away from a reactive state and into a secure, proactive, readily defensible posture.
How can BuddoBot help?
Our CAE service emulates real adversaries. Our deep experience in the field reveals one common denominator: adversaries are opportunistic and patient. They have unlimited time to plan, prepare, and exploit your defenses. Our team leverages known tactics, techniques, and procedures (TTPs) and red team strategies to give you the best possible answer to the question: “Can I be breached?”
Over the course of the campaign, you will receive continuous external threat campaigns and scheduled assumed breach campaigns by our offensive security engineers. This can include a full suite of capabilities:
-
Advanced phishing and vishing campaigns
-
External infrastructure testing
-
Web application testing
-
Assumed breach internal testing
-
Attack surface management
-
Threat intelligence reporting
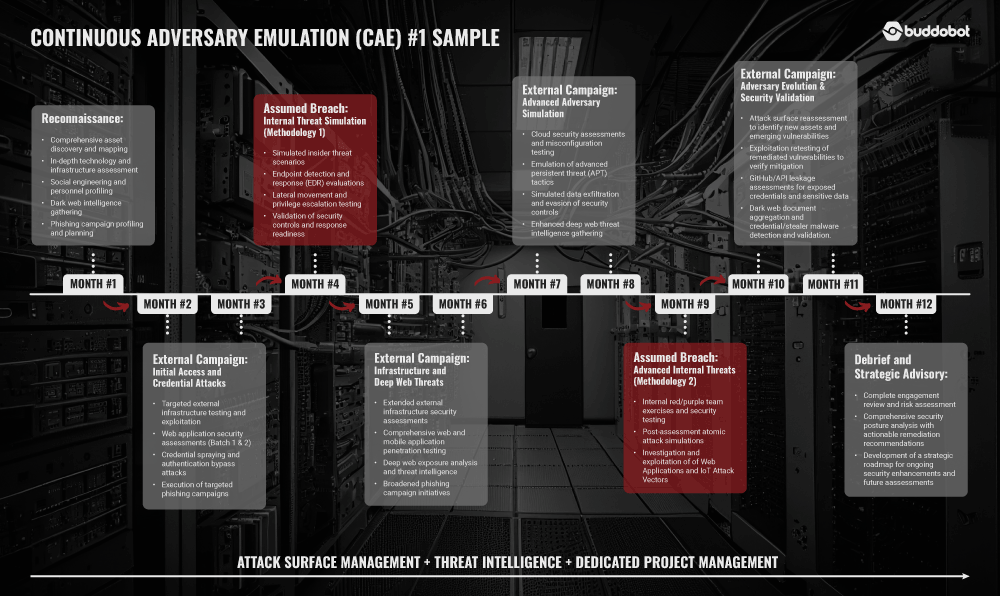
Each engagement is customized to deliver maximum value based on each customer’s needs or requirements. We also pride ourselves on our ability to help you detect and mitigate beyond the standard types of reports we see in the industry. See below for a sample one-year CAE engagement.
We are expertise first, tools second. Unfortunately, the industry is saturated with automated tools. We are here to shake things up and show the world that you can’t just rely on point-and-click testing to truly emulate the adversary.
Quality & Expertise Matter
BuddoBot has a long history of working with the best security testers in the industry. Our staff of offensive security engineers has decades of experience in offensive security. They have presented and contributed to the community at world-renowned conferences such as DEF CON, BlackHat, OWASP, RSA, Security BSides, SANS, IANS, ISSA, and more. Their contributions are often cited in books and trainings worldwide.
Our dedicated team of offensive security engineers works hand-in-hand with the broader security researcher community. Thanks to our extensive connections in the bug bounty space, we have relationships with some of the most talented and experienced specialists in various domains of offensive security. We leverage this network of experts throughout your campaign to ensure you receive the highest quality testing possible. Our collaborative approach allows us to tap into the collective knowledge and experience of the broader security community, enabling us to provide unparalleled insights and recommendations to enhance your security posture.

